Best Practices for Construction Site Security
21st Century Construction Security Means Covering Every Angle
Security Threats: An Introduction
Construction sites, by their very nature, can invite access control breaches. Located in accessible public places, utilizing open floor plans, loaded with valuable materials and tools, and attracting attention with their size and noise, construction sites are a burglar’s dream.
The National Equipment Register estimates that $400 million worth of heavy equipment is stolen from construction sites every year. That’s not including theft of building materials (which are undergoing a major price hike) or tools. Work stoppages, associated with bust cycles and health related lockdowns, leave sites vacant and especially vulnerable for long periods of time. And theft need not only come from outsiders; a major portion of project site theft comes from disgruntled or opportunistic employees who have the inside scoop on the site.
Construction sites may invite opportunistic outsiders beyond thieves; vandals and arsonists can wreak their own kind of night time havoc. Daytime intruders (trespassers, competitors on reconnaissance, protestors, violent offenders) may practice identity fraud in order to pass through check-in stations, or may attempt assaults on workers. While potential hires should not be treated with undue suspicion, an investigation into their backgrounds may also reveal potential safety issues.
Knowing that threats can come from a variety of different sources, how should the modern contractor react? By employing their own variety of security protocols, of course. A systematic, holistic approach to site protection means recognizing that the world presents a diverse range threats and problematic situations to resolve. By integrating several safeguards into a unified approach, managers can cut bad actors off at the pass, stay several steps ahead of criminal planning, and stymie access breaches once and for all.
The National Equipment Register estimates that $400 million worth of heavy equipment is stolen from construction sites every year. That’s not including theft of building materials (which are undergoing a major price hike) or tools. Work stoppages, associated with bust cycles and health related lockdowns, leave sites vacant and especially vulnerable for long periods of time. And theft need not only come from outsiders; a major portion of project site theft comes from disgruntled or opportunistic employees who have the inside scoop on the site.
Construction sites may invite opportunistic outsiders beyond thieves; vandals and arsonists can wreak their own kind of night time havoc. Daytime intruders (trespassers, competitors on reconnaissance, protestors, violent offenders) may practice identity fraud in order to pass through check-in stations, or may attempt assaults on workers. While potential hires should not be treated with undue suspicion, an investigation into their backgrounds may also reveal potential safety issues.
Knowing that threats can come from a variety of different sources, how should the modern contractor react? By employing their own variety of security protocols, of course. A systematic, holistic approach to site protection means recognizing that the world presents a diverse range threats and problematic situations to resolve. By integrating several safeguards into a unified approach, managers can cut bad actors off at the pass, stay several steps ahead of criminal planning, and stymie access breaches once and for all.


The Site Security Toolbox
Any security approach should integrate aspects of all of the following:
• Research and planning
• Physical barriers
• Psychological deterrence
• Security personnel
• Cameras and other recording equipment
• Inventory control
• Human resources and management
• Identity management systems
Let’s examine each of these in order.
• Research and planning
• Physical barriers
• Psychological deterrence
• Security personnel
• Cameras and other recording equipment
• Inventory control
• Human resources and management
• Identity management systems
Let’s examine each of these in order.
Conventional Methods
The first step to securing any construction site begins with the planning phase. Before a project even begins, a security assessment of local risks should be performed. That assessment should then become a site-specific plan, written out as a policy document. A consultative relationship should be established with local law enforcement, and internal company experts should be called upon for their expertise. Responsibilities for supervising security can be assigned to various managers, who should also impart an ethic of security to their workforce. The plan can be periodically reviewed and updated, as risks on the ground evolve.
Physical barriers are an obvious and essential component of defending a site. This means erecting a fence around the site that can be fully locked at night time, with manned access control points that allow flowthrough during the day. Said boundary can include material that deters fence climbing, and should be fully illuminated to expose potential climbers. Physical barriers don’t just include the walls, either. Keeping everything that can be locked, locked down, adds another layer of defense. Ensuring that vehicles and heavy equipment are secured with heavy steel locks, disabled, or protected with antitheft devices can prevent them from being driven off site at night. Vehicles can be outfitted with keyless ignition systems that require a unique PIN for operation. Establishing separate storage areas for more portable items such as personal affects, materials, and tools provides further barriers to theft. Such storage areas can be shipping containers, storage trailers or other units, and should also be guarded by heavy locks. Ensuring that fuel and oil cans are stowed away, and gas tank caps are locked, will also suck the oxygen out of arson attempts.
Visual and audio deterrence adds a more psychological advantage to security plans. Warning signs placed around the site can be a reminder to thieves that detection systems will enable their prosecution. The use of lights to illuminate the site after hours will eliminate visual cover for criminal activity, while obviously placed cameras will show that every action is recorded. Motion- activated lights, sirens and alarms can be utilized to create more panic for intruders. Incorporating visible on-site guards with monitoring stations and patrols are the most powerful deterrent, discouraging not only break ins, but minor probing attempts as well. Finally, simply staying on top of your security- from maintaining all systems, to responding to minor incursions- will show offenders that they do not have the opportunity to escalate.
For those that do choose to use camera or CCTV systems, there is a vast range of tactical and technological options available. Cameras should be effectively placed so as to ensure full site coverage; alternately, installing PTZ cameras with full 360° rotation can be effective. All cameras should remain out of the reach of intruders. Motion recording and thermal detection can enhance video capture and even trigger automated alerts. 24/7 recording, long range surveillance, advanced analytics, and facial recognition software can provide prosecutorial evidence after an intrusion. Finally, live monitoring by guards or off premise experts, combined with effective coordination with law enforcement, is the most powerful tool that managers can use to apprehend intruders.
Maintaining an inventory control system for all tools, materials, and equipment is essential for determining and rectifying theft. This not only includes recording identifiers like serial numbers, license plate numbers, etc. but registering them with state and local authorities. All items should be photographed in their original condition, as well as marked by the company in an obvious way. Verifying all deliveries, as well as creating a check-out process for tools or equipment keys, can eliminate much of the guesswork around theft and vandalism. At higher levels of inventory control, heavy equipment can be outfitted with GPS beacons (tracking), and smaller equipment and tools can all be RFID chipped or labeled with QR codes.
The construction workforce itself must be managed for security risks. Disgruntled employees are more likely to steal material from the site, and those who get away with theft are emboldened to escalate their sabotage. For these reasons, employers should strive to support the needs of their workforce, and address their grievances, while swiftly punishing any acts of theft or vandalism among the workers. Failure to adequately screen or drug test workers prior to employment constitutes a final potential security breach with your personnel.
Physical barriers are an obvious and essential component of defending a site. This means erecting a fence around the site that can be fully locked at night time, with manned access control points that allow flowthrough during the day. Said boundary can include material that deters fence climbing, and should be fully illuminated to expose potential climbers. Physical barriers don’t just include the walls, either. Keeping everything that can be locked, locked down, adds another layer of defense. Ensuring that vehicles and heavy equipment are secured with heavy steel locks, disabled, or protected with antitheft devices can prevent them from being driven off site at night. Vehicles can be outfitted with keyless ignition systems that require a unique PIN for operation. Establishing separate storage areas for more portable items such as personal affects, materials, and tools provides further barriers to theft. Such storage areas can be shipping containers, storage trailers or other units, and should also be guarded by heavy locks. Ensuring that fuel and oil cans are stowed away, and gas tank caps are locked, will also suck the oxygen out of arson attempts.
Visual and audio deterrence adds a more psychological advantage to security plans. Warning signs placed around the site can be a reminder to thieves that detection systems will enable their prosecution. The use of lights to illuminate the site after hours will eliminate visual cover for criminal activity, while obviously placed cameras will show that every action is recorded. Motion- activated lights, sirens and alarms can be utilized to create more panic for intruders. Incorporating visible on-site guards with monitoring stations and patrols are the most powerful deterrent, discouraging not only break ins, but minor probing attempts as well. Finally, simply staying on top of your security- from maintaining all systems, to responding to minor incursions- will show offenders that they do not have the opportunity to escalate.
For those that do choose to use camera or CCTV systems, there is a vast range of tactical and technological options available. Cameras should be effectively placed so as to ensure full site coverage; alternately, installing PTZ cameras with full 360° rotation can be effective. All cameras should remain out of the reach of intruders. Motion recording and thermal detection can enhance video capture and even trigger automated alerts. 24/7 recording, long range surveillance, advanced analytics, and facial recognition software can provide prosecutorial evidence after an intrusion. Finally, live monitoring by guards or off premise experts, combined with effective coordination with law enforcement, is the most powerful tool that managers can use to apprehend intruders.
Maintaining an inventory control system for all tools, materials, and equipment is essential for determining and rectifying theft. This not only includes recording identifiers like serial numbers, license plate numbers, etc. but registering them with state and local authorities. All items should be photographed in their original condition, as well as marked by the company in an obvious way. Verifying all deliveries, as well as creating a check-out process for tools or equipment keys, can eliminate much of the guesswork around theft and vandalism. At higher levels of inventory control, heavy equipment can be outfitted with GPS beacons (tracking), and smaller equipment and tools can all be RFID chipped or labeled with QR codes.
The construction workforce itself must be managed for security risks. Disgruntled employees are more likely to steal material from the site, and those who get away with theft are emboldened to escalate their sabotage. For these reasons, employers should strive to support the needs of their workforce, and address their grievances, while swiftly punishing any acts of theft or vandalism among the workers. Failure to adequately screen or drug test workers prior to employment constitutes a final potential security breach with your personnel.

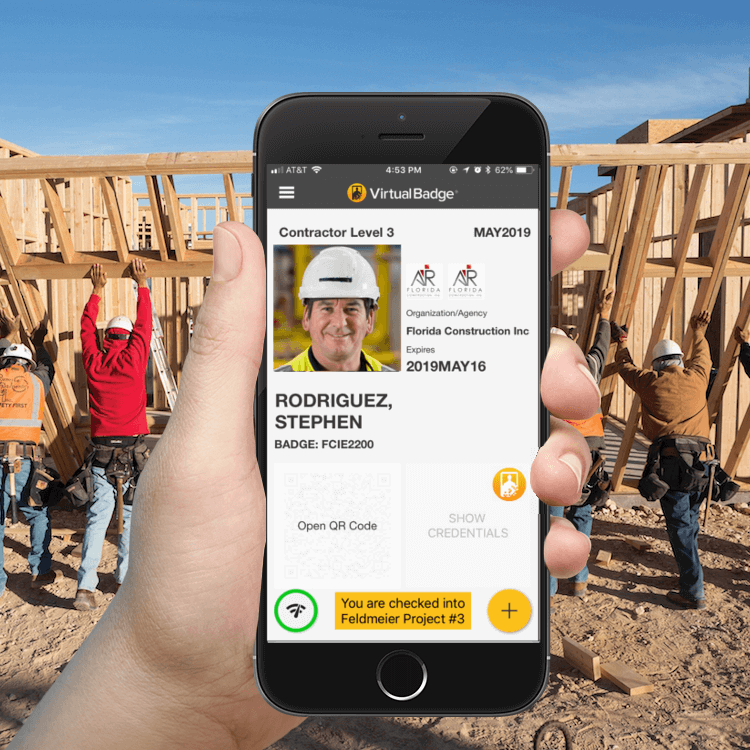
Innovative methods: Identity Management
While the above-mentioned methods are excellent ways of stopping overt intruders, more sophisticated methods are needed to demarcate covert intruders from company employees. Virtual badges for employees are an example of an identity/workforce management system that can track an entire construction workforce: who they are (and aren’t), where they’ve been, and when they arrived and left.
Prior to arriving on site (or at their first arrival), workers submit their identification documentation for badge approval. Once approved by administrators, digital ID badges indicate the presence of official employees, subcontractors, vendors or visitors. With site perimeter fencing established, your access control points should only grant access to virtual badge users. A seamless check-in process, enabled by a simple badge scan, allows for rapid access. And because digital ID badges are secured using unique QR identifiers- and can’t be faked, like traditional hard badges- imposters won’t make it through the gate.
The badge approval process can be linked to passing a background check and drug test, filtering out potentially dangerous personnel. Automated rolling background checks can be connected to virtual badges, meaning that employees and subs are periodically screened over time. Should a follow-up background check fail, the associated badge will automatically terminate, preventing the holder from future site access. Any contract terminating event, for that matter, can result in a badge being deleted. Such flexibility affords site managers the ability to truly deny access to delinquent or disgruntled workers (who may be more likely to damage company property).
Digital ID badges support biometric integrations, like fingerprint analysis and facial recognition. Such biometric markers can be read, via smart device, during the badge creation process, or even the worksite check-in. While virtual badging systems are quite secure on their own, discriminating managers can support biometric integrations for added peace of mind.
Sites without hard perimeters can implement geofencing- an automatic check-in process whenever and wherever badge holders cross into the site. Even with a porous site, unapproved personnel will be unable to produce a badge upon request. Approved badge holders can be tracked down to their assigned geographic zones- an especially useful tool for security incident detective work. Being able to narrow down who was where, and thus who shouldn’t have been there, makes finding offenders that much easier.
In the unfortunate and unlikely event that a security issue does take place during regular hours, every badge holder can receive alerts (via their badge) that warn them to steer clear of the incident.
Prior to arriving on site (or at their first arrival), workers submit their identification documentation for badge approval. Once approved by administrators, digital ID badges indicate the presence of official employees, subcontractors, vendors or visitors. With site perimeter fencing established, your access control points should only grant access to virtual badge users. A seamless check-in process, enabled by a simple badge scan, allows for rapid access. And because digital ID badges are secured using unique QR identifiers- and can’t be faked, like traditional hard badges- imposters won’t make it through the gate.
The badge approval process can be linked to passing a background check and drug test, filtering out potentially dangerous personnel. Automated rolling background checks can be connected to virtual badges, meaning that employees and subs are periodically screened over time. Should a follow-up background check fail, the associated badge will automatically terminate, preventing the holder from future site access. Any contract terminating event, for that matter, can result in a badge being deleted. Such flexibility affords site managers the ability to truly deny access to delinquent or disgruntled workers (who may be more likely to damage company property).
Digital ID badges support biometric integrations, like fingerprint analysis and facial recognition. Such biometric markers can be read, via smart device, during the badge creation process, or even the worksite check-in. While virtual badging systems are quite secure on their own, discriminating managers can support biometric integrations for added peace of mind.
Sites without hard perimeters can implement geofencing- an automatic check-in process whenever and wherever badge holders cross into the site. Even with a porous site, unapproved personnel will be unable to produce a badge upon request. Approved badge holders can be tracked down to their assigned geographic zones- an especially useful tool for security incident detective work. Being able to narrow down who was where, and thus who shouldn’t have been there, makes finding offenders that much easier.
In the unfortunate and unlikely event that a security issue does take place during regular hours, every badge holder can receive alerts (via their badge) that warn them to steer clear of the incident.
Conclusion
The world presents a range of security risks that can threaten any construction project. Fortunately, an even greater range of defensive precautions are available to managers and contractors. By first understanding the specific threats a site could face, and then crafting an integrated security plan, managers can feel more secure in their charges. If possible, each aspect of the security toolbox should be implemented. Without reservation, conventional area denial methods should be combined with recording equipment, inventory tracking, workforce screening, and innovative identity management systems.
If you’ve already implemented more tried and true methods, it might be time to give virtual badges a closer look. Unified security plans should incorporate technology that can manage worker statuses, prevent identity fraud and daytime trespass, and disseminate mass alerts. If you’d like to infuse old school practices with connectivity-enabled safeguards, our knowledgeable experts can help guide you along the way.
If you’ve already implemented more tried and true methods, it might be time to give virtual badges a closer look. Unified security plans should incorporate technology that can manage worker statuses, prevent identity fraud and daytime trespass, and disseminate mass alerts. If you’d like to infuse old school practices with connectivity-enabled safeguards, our knowledgeable experts can help guide you along the way.

